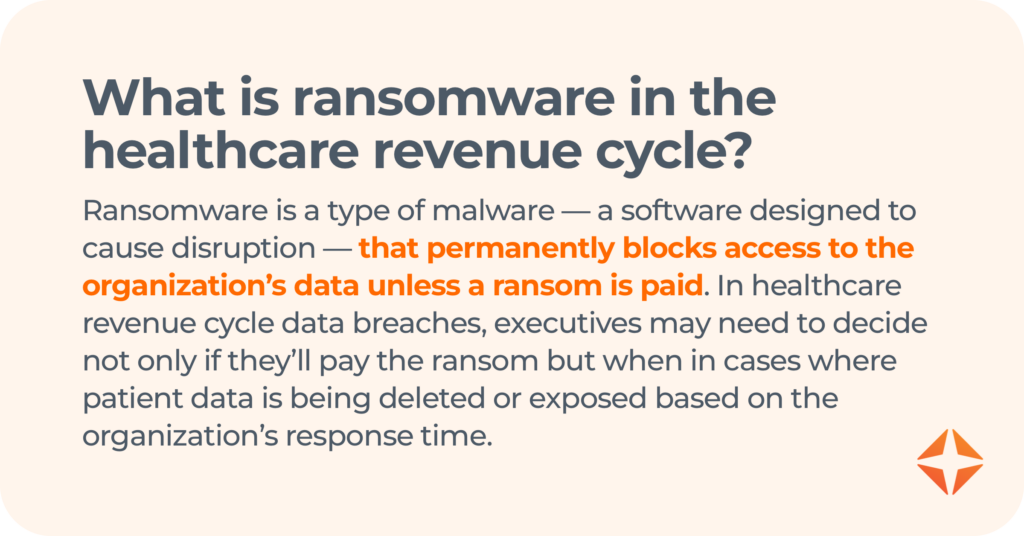
If you’re a leader in healthcare revenue cycle management, cybersecurity threats are a top concern — and they have to be when more than 132 million Americans (roughly 40% of the U.S. population) were affected by health-record data breaches in 2023 alone.
This was called into sharp focus recently, when a cyberattack breached the network of a health IT giant, disrupting operations for healthcare organizations across the U.S.
While that situation is complex and ongoing, there are proven strategies proactive organizations can implement now to reduce future cybersecurity threats.
TIP 1: REDUCING FUTURE CYBERSECURITY THREATS IN HEALTHCARE
Assess your vendor’s ability to serve + support you
When the unthinkable happens, you need to know you’re working with a trustworthy partner who has the same values you do. You also need to be confident in their ability to support an organization of your size, scope, and with your specific data-protection needs.
Ideally, you’ll explore all of this before a crisis happens. But if you find yourself shopping for a new vendor after — or even during — a crisis, ask potential vendors:
- What is your average implementation satisfaction score?
- How often do you meet or exceed implementation timelines?
- What is your average client support satisfaction score?
- How long does it take to reach a live support representative?
- What is your average turnaround time on support case resolution?
If your vendor can’t or won’t offer those metrics, find an RCM partner who provides a better experience.
TIP 2: REDUCING FUTURE CYBERSECURITY THREATS IN HEALTHCARE
Check vendor certifications + assessments
Vendors who value security will leverage leading security performance-evaluation firms to maintain up-to-date, secure practices.
Ask about these common certifications and standards:
1. SOC 2 Type II
SOC 2 is a security framework that specifies how organizations will protect client data from security incidents and unauthorized access. It ensures a SaaS provider is managing the environment to the ‘trust service principle’ — prioritizing security, privacy, availability, confidentiality, and processing integrity.
Make sure your vendor:
- Adheres to SOC 2 Type II because that provides evidence of long-term, ongoing processes that protect customer data
- Keeps this certification current since some vendors will achieve it and then allow it to lapse
2. HITRUST r2
The HITRUST Common Security Framework (CSF) helps healthcare organizations prove they are operating securely and compliantly while keeping personal health information (PHI) secure. Make sure your vendors adhere to the HITRUST r2 Validated Assessment as that is the gold standard for information protection assurances.
3. PCI DSS
The Payment Card Industry Data Security Standard (PCI DSS) validates that any organization processing credit card payments is authorized to do so.
HIPAA compliance
The Health Insurance Portability and Accountability Act (HIPAA) sets the security and privacy regulations required to protect sensitive patient health information. It’s enforced by the Office of Civil Rights and is legally required for any healthcare or IT service provider that accesses PHI.
4. Security information and event Management (SIEM) system
SIEM systems collect and analyze data from sources across the organization’s network — firewalls, intrusion-detection systems, endpoint security solutions — to help identify unusual activity that may indicate a threat.

TIP 3: REDUCING FUTURE CYBERSECURITY THREATS IN HEALTHCARE
Ask partners + vendors key security questions
When you partner with a vendor who can impact your cash flow, you must be confident they can keep your data secure and act swiftly when threats occur.
Ask partners + vendors: | The answer should include: |
| How do you monitor systems for suspicious activity?
|
|
| What’s your process for assessing vulnerabilities in your systems and network?
|
|
| What is your recovery strategy if you’re targeted or hacked?
|
|
Setting expectations — on both sides, in advance — will help everyone maintain order so you can act fast to keep data as secure as possible in the event of a cybersecurity attack.
TIP 4: REDUCING FUTURE CYBERSECURITY THREATS IN HEALTHCARE
Strengthen existing security + access controls
Security and access control are essential measures that determine who can access your data, resources, and apps. Make sure your organization is leveraging all available options to safeguard data and prevent unauthorized access.
Ask your IT department to:
1. Require frequent password rotations.
Schedule regular password changes across your organization and systems. Consider increasing the minimum password length and special-character requirements.
2. Implement two-factor authentication.
Consider asking for two separate, distinct forms of identification to access your systems, phones, and even buildings.
3. Review IP whitelisting settings.
IP whitelisting lets organizations grant access to trustworthy IP addresses, but it’s not something you should “set and forget.” Review IP whitelisting periodically so you can restrict unauthorized access to systems and networks and ensure every IP address with access should, in fact, have it.
4. Monitor user activity.
Monitor user activity on the network to detect suspicious behavior, such as unauthorized access attempts or data exfiltration.
TIP 5: REDUCING FUTURE CYBERSECURITY THREATS IN HEALTHCARE
Train employees regularly on data security + compliance
While most RCM employees understand the magnitude of cybersecurity threats in healthcare, regular training is still critical. Not only will it show staff the risks and threats your organization faces, but it will also give them the knowledge to identify potential threats and the tools to report them.
Make sure every employee completes regular training on the most common methods of cyberattack, including:
1. Email
According to the HIPAA Journal, phishing is a leading cause of healthcare data breaches — and attacks are increasing. Malicious links, attachments, and downloads are common ways attackers gain access to systems. Give your team tips for spotting malicious content to prevent network infiltration.
2. QR codes
Today’s attackers have also expanded their phishing efforts to include QR phishing. An attacker will send the target a code and convince them to scan it for a seemingly valid reason. That can lead to compromised credentials, data breaches, or ransomware infections.
3. Mobile
Employees often unknowingly use personal or work mobile devices in ways that make them susceptible to mobile-based attacks.
- If you allow employees to access work information via personal devices, make sure you activate the necessary controls (company portal applications for remote management, password-strength requirements, etc.).
- Teach employees about smishing (fake SMS/text messages) and vishing (fraudulent phone calls), which can easily trick victims into providing sensitive information via text or phone call.
4. Working remotely
With remote work now a permanent part of revenue cycle management, employees must (1) know the risks of working outside a secure office environment, and (2) follow best practices when doing so. Consider who needs to be using a virtual private network (VPN), who should come into the office to perform specific tasks, etc.
Remember to include compliance and regulatory training in your schedule as well. Accidental HIPAA violations are much easier to avoid when training outlines what each staff member needs to do to stay compliant while performing their specific duties.
Are you facing revenue cycle disruption?
Get the experience you deserve